Facial biometrics: how smartphones can recognize us

geralt/Pixabay
Mohamed Daoudi, IMT Lille Douai – Institut Mines-Télécom
Welcome to the new era: that of facial biometrics. The launch of the iPhone X, a smartphone featuring Face ID facial recognition, demonstrated that this technology has now reached full maturity. This became possible with the introduction of miniature 3D sensors with high-level computing power, combined with extremely efficient learning algorithms such as deep learning.
But what is facial recognition? It means identifying that two faces are identical despite changes caused by lighting conditions, pose and facial expressions. Generally speaking, this means finding distances within the face that can be used to identify any changes to the face.

In 2014, researchers from Facebook published an article called “DeepFace: Closing the Gap to Human-Level Performance in Face Verification”. To prevent the problems caused by changes in pose, a step was introduced to align the 2D face to a 3D model of the face. The next step involved a deep learning process using a network of artificial neurons consisting of 120 million connections. The learning set was composed of 4.4 million faces of celebrities. The network of neurons was trained to recognize the variances in the faces. The algorithm made it possible to determine if two photographed faces belonged to the same person with a specified accuracy of 97.35%.
In 2015, researchers from Google published an article entitled “FaceNet: A Unified Embedding for Face Recognition and Clustering”. They showed that they were able to achieve a recognition rate of 99.63% using a database of 2D faces captured in an uncontrolled environment. To accomplish this, the authors proposed the use of a neural network consisting of eleven convolutional layers and three connected layers. The idea was to ensure that an image of a specific person would be closer to all the other images of that same person (referred to as positive) than to the images of other people (referred to as negative). The learning was carried out using a database of 200 million face images from 8 million people.
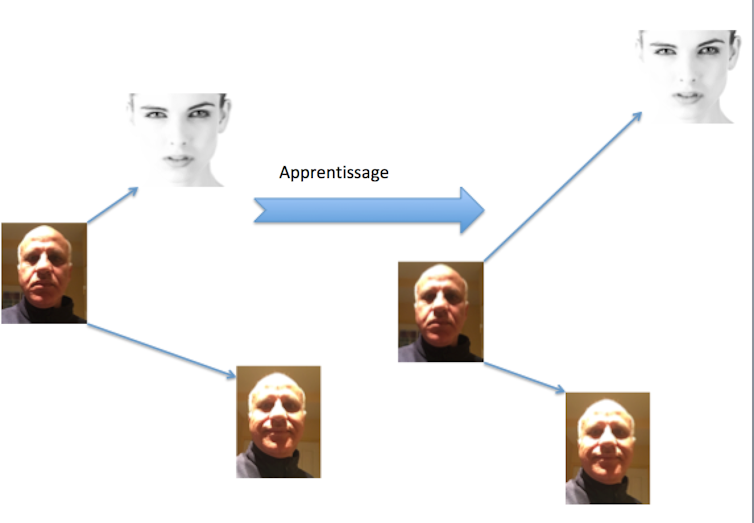
However, the DeepFace and FaceNet experiments were both based on private databases that are not available to the scientific community. A team from the University of Oxford proposed to collect data from the web and has established a database of 2.6 million faces from 2,622 people and has proposed a network architecture called VGG-face consisting of 16 convolutional layers and 3 fully connected layers. Today this architecture is widely used by the computer vision community.
Yet the face is not only a 2D image; it is also a three-dimensional image. Facial biometrics can be used because 3D scanning technologies can scan faces. The major advantage of using 3D in this context is that the facial recognition algorithms are resistant to changes in lighting and pose. Recent work published in 2013 by our team at IMT Lille Douai in the journal IEEE TPAMI, “3D face recognition under expressions, occlusions, and pose variations” showed the advantage of this process. In this article, we proposed to compare two 3D faces by comparing two sets of curves that locally represent the shape of a 3D face. We obtained a recognition rate of 97% (using the testing framework Face Recognition Grand Challenge). The results obtained from several international tests reveal the advantages of 3D faces in facial biometrics systems.

Now let us get back to the iPhone X and its 3D technology for facial recognition. A feat made possible by the introduction of miniature 3D sensors on the front of the device: a projector sends 30,000 invisible points onto the user’s face, which are used to create a 3D model of the face. According to Apple, Face ID cannot be fooled by a mere photograph of a face, since the recognition is achieved with a 3D sensor that measures depth.
The original French version of this article was translated to English by the Institut Mines-Télécom.
Mohamed Daoudi, Professeur à l’IMT Lille Douai, Centre de recherche en informatique, signal et automatique de Lille, IMT Lille Douai – Institut Mines-Télécom
This article is republished from The Conversation under a Creative Commons license. Read the original article.




This is what we know of, not what has been hidden from us. I’m sure each one of us is tracked, of course we are. When AI takes over to decides the needs of the human race then we in deep shit.
Views: 6
0
0
Share This
Read Time:5 Minute, 12 Second
What is Pegasus? A cybersecurity expert explains how the spyware invades phones and what it does when it gets in
What is Pegasus A cybersecurity expert explainsA woman holds a phone in front of the office of NSO Group, which makes a tool that can see and hear everything a phone is used for.
Jack Guez/AFP via Getty Images
Bhanukiran Gurijala, West Virginia University
End-to-end encryption is technology that scrambles messages on your phone and unscrambles them only on the recipients’ phones, which means anyone who intercepts the messages in between can’t read them. Dropbox, Facebook, Google, Microsoft, Twitter and Yahoo are among the companies whose apps and services use end-to-end encryption.
This kind of encryption is good for protecting your privacy, but governments don’t like it because it makes it difficult for them to spy on people, whether tracking criminals and terrorists or, as some governments have been known to do, snooping on dissidents, protesters and journalists. Enter an Israeli technology firm, NSO Group.
The company’s flagship product is Pegasus, spyware that can stealthily enter a smartphone and gain access to everything on it, including its camera and microphone. Pegasus is designed to infiltrate devices running Android, Blackberry, iOS and Symbian operating systems and turn them into surveillance devices. The company says it sells Pegasus only to governments and only for the purposes of tracking criminals and terrorists.
How it works
Earlier version of Pegasus were installed on smartphones through vulnerabilities in commonly used apps or by spear-phishing, which involves tricking a targeted user into clicking a link or opening a document that secretly installs the software. It can also be installed over a wireless transceiver located near a target, or manually if an agent can steal the target’s phone.
Pegasus can infiltrate a smartphone via the widely used messaging app WhatsApp without the phone’s user noticing.
Christoph Scholz/Flickr, CC BY-SA
Since 2019, Pegasus users have been able to install the software on smartphones with a missed call on WhatsApp, and can even delete the record of the missed call, making it impossible for the the phone’s owner to know anything is amiss. Another way is by simply sending a message to a user’s phone that produces no notification.
This means the latest version of this spyware does not require the smartphone user to do anything. All that is required for a successful spyware attack and installation is having a particular vulnerable app or operating system installed on the device. This is known as a zero-click exploit.
Once installed, Pegasus can theoretically harvest any data from the device and transmit it back to the attacker. It can steal photos and videos, recordings, location records, communications, web searches, passwords, call logs and social media posts. It also has the capability to activate cameras and microphones for real-time surveillance without the permission or knowledge of the user.
Who has been using Pegasus and why
NSO Group says it builds Pegasus solely for governments to use in counterterrorism and law enforcement work. The company markets it as a targeted spying tool to track criminals and terrorists and not for mass surveillance. The company does not disclose its clients.
The earliest reported use of Pegasus was by the Mexican government in 2011 to track notorious drug baron Joaquín “El Chapo” Guzmán. The tool was also reportedly used to track people close to murdered Saudi journalist Jamal Khashoggi.
It is unclear who or what types of people are being targeted and why. However, much of the recent reporting about Pegasus centers around a list of 50,000 phone numbers. The list has been attributed to NSO Group, but the list’s origins are unclear. A statement from Amnesty International in Israel stated that the list contains phone numbers that were marked as “of interest” to NSO’s various clients, though it’s not known if any of the phones associated with numbers have actually been tracked.
A media consortium, the Pegasus Project, analyzed the phone numbers on the list and identified over 1,000 people in over 50 countries. The findings included people who appear to fall outside of the NSO Group’s restriction to investigations of criminal and terrorist activity. These include politicians, government workers, journalists, human rights activists, business executives and Arab royal family members.
Other ways your phone can be tracked
Pegasus is breathtaking in its stealth and its seeming ability to take complete control of someone’s phone, but it’s not the only way people can be spied on through their phones. Some of the ways phones can aid surveillance and undermine privacy include location tracking, eavesdropping, malware and collecting data from sensors.
Law enforcement agencies use cell site simulators like this StingRay to intercept calls from phones in the vicinity of the device.
U.S. Patent and Trademark Office via AP
Governments and phone companies can track a phone’s location by tracking cell signals from cell tower transceivers and cell transceiver simulators like the StingRay device. Wi-Fi and Bluetooth signals can also be used to track phones. In some cases, apps and web browsers can determine a phone’s location.
Eavesdropping on communications is harder to accomplish than tracking, but it is possible in situations in which encryption is weak or lacking. Some types of malware can compromise privacy by accessing data.
The National Security Agency has sought agreements with technology companies under which the companies would give the agency special access into their products via backdoors, and has reportedly built backdoors on its own. The companies say that backdoors defeat the purpose of end-to-end encryption.
The good news is, depending on who you are, you’re unlikely to be targeted by a government wielding Pegasus. The bad news is, that fact alone does not guarantee your privacy.
[Understand new developments in science, health and technology, each week. Subscribe to The Conversation’s science newsletter.]
Bhanukiran Gurijala, Assistant Professor of Computer Science & Information Systems, West Virginia University
This article is republished from The Conversation under a Creative Commons license. Read the original article.
How smartphones can recognize us
Share
Related Posts:What are dark patterns? An online media expert explainsWhat’s a ghost kitchen? A food industry expert explainsHow to avoid food-borne illness – a nutritionist explainsExpert Tips for Welcoming a KittenExpert tips to maximize your victory gardenExpert tips for maintaining your pet’s healthy weight